The name of the author who created the presentation is included in ____.
A. the presentation evaluation
B. metadata
C. the off-slide content
D. the digital signature encryption text box
Answer: B
You might also like to view...
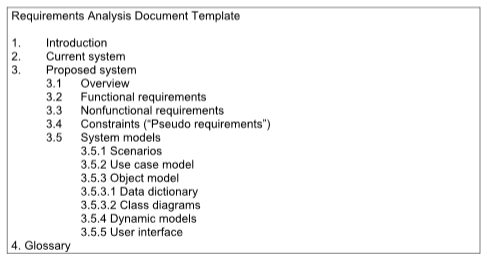
Reverse engineer the requirements of the Heathrow airport luggage system and communicate your results using the Requirements Analysis Document template presented in the lecture.
Questions to ask:
• How are the bags stored after passengers have checked, but before they
enter the plane?
• How are the bags retrieved from the storage area?
• What about existing luggage systems (“legacy systems”)?
• Scalability: How many users should the new luggage system support? How can
this be tested before deployment?
• Throughput: How many suit cases/hour need to be supported?
The first step when saving a file for someone running Word 97-2003 is to click the ________ tab
Fill in the blank(s) with correct word
3G, 4G, and LTE are all terms that refer to mobile Internet connectivity.
Answer the following statement true (T) or false (F)
When the Magic Wand tool is selected, the ____ on the options bar lets you select pixels that are next to one another.
A. Tolerance check box B. Anti-alias check box C. Contiguous check box D. Use All Layers check box