?Which of the following is the correct description of a firewall?
A. ?It is a software that deletes viruses from attachments.
B. ?It is hardware that prevents unauthorized data to enter the private network.
C. It is a software and hardware combination that limits the incoming and outgoing Internet traffic.
D. ?It is a concept used in developing security policies.
Answer: C
You might also like to view...
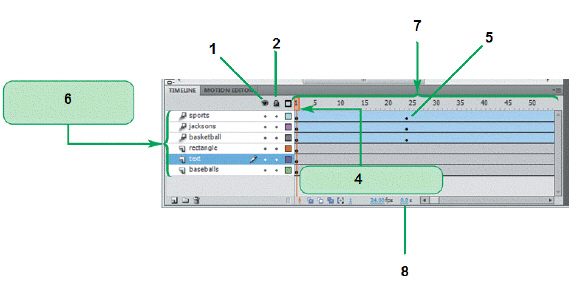 The item marked ____ in the accompanying figure is the playhead.
The item marked ____ in the accompanying figure is the playhead.
A. 2 B. 4 C. 5 D. 8
Which of the following could not be done using an aggregate function?
What will be an ideal response?
What happens when you finish making changes with a YaST module?
What will be an ideal response?
Which of the following statements about program documentation and data names is false?
A. General documentation occurs at the beginning of the program B. Module documentation occurs within functions C. Intelligent data names cannot be abbreviated D. Data names should match the terminology of the user as closely as possible E. The use of generic names, such as amount, should be avoided