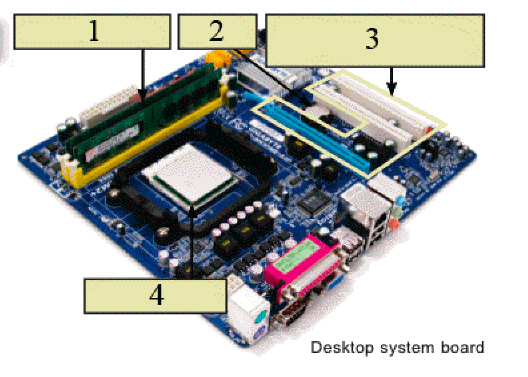
 In the figure above, the object indicated by item ____ is the main processing device in your PC.
In the figure above, the object indicated by item ____ is the main processing device in your PC.
A. 2
B. 3
C. 4
D. 1
Answer: C
You might also like to view...
Draw a UML activity diagram describing the dependency between activities for a life cycle in which requirements, design, implementation, test, and maintenance occur concurrently. (This is called an evolutionary life cycle.)
What will be an ideal response?
Which of the following processes guarantees that packets are ordered properly and protects against missing segments?
A. watchdog B. keep-alive C. handshake D. sequence and acknowledgment
An easy way to begin creating a blog is to use Word's Blog post ________
Fill in the blank(s) with correct word
Recently an attack occurred whereby the attacker gained access to the database with admin privileges. Even though the IDS alerted the team that unusual access was occurring, and they changed the admin password, the attacker continued to access the database until it was disconnected from the network. What type of attack allowed him to do so?
A. SQL injection B. XSS C. race condition D. DDoS