Many companies require ____ to ensure privacy by preventing bystanders from viewing display contents.
A. screen filters
B. LoJack for Laptops
C. personal identification numbers
D. firewalls
Answer: A
Computer Science & Information Technology
You might also like to view...
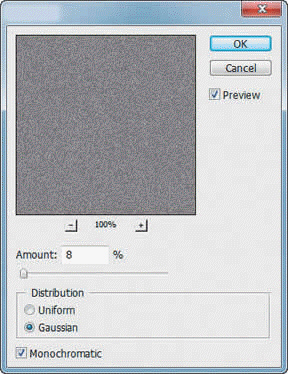 Which of the following can be accomplished by using the dialog box in the accompanying figure?
Which of the following can be accomplished by using the dialog box in the accompanying figure?
A. add sharpness to artwork B. create a consistent texture across an image C. both a. and b. D. neither a. nor b.
Computer Science & Information Technology
A node with k < m subtrees contains k subtrees and ____ data entries.
A. k / 2 B. k - 2 C. k - 1 D. k
Computer Science & Information Technology
What work products result from the requirements engineering process?.
What will be an ideal response?
Computer Science & Information Technology
Distinguish between a major fault and a minor fault.
What will be an ideal response?
Computer Science & Information Technology