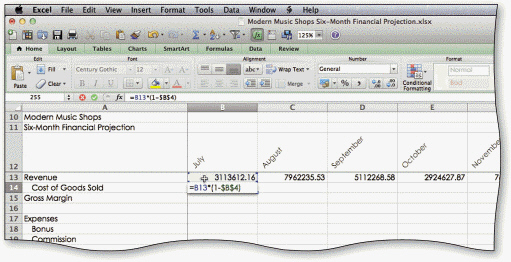
 In the accompanying figure, the formula in cell B14 contains an absolute reference.
In the accompanying figure, the formula in cell B14 contains an absolute reference.
Answer the following statement true (T) or false (F)
True
You might also like to view...
Consider the relation schema corresponding to the IsA hierarchy in Figure 4.6. Assume that this schema has one relation per entity. (Consult Section 4.4 to refresh your memory about translation of IsA hierarchies into the relational model.) Write the following queries both in tuple and domain relational calculus:
a. Find the names of all sophomores in the computer science major. b. Find the names of all students in the computer science major. c. Find all departments where some technician has every specialization that any other technician (in the same or another department) has.
The word shown in bold is spelled correctly in the following sentence.The team scored early goals in both halfs of the game.?
Answer the following statement true (T) or false (F)
Cyberterrorists hack systems to conduct terrorist activities via network or Internet pathways. _________________________
Answer the following statement true (T) or false (F)
Outlook is an example of an email program.
Answer the following statement true (T) or false (F)