A client server authentication method that can be implemented in many different networking devices, such as routers, firewalls, and access points is known as __________.
Fill in the blank(s) with the appropriate word(s).
RADIUS
You might also like to view...
Every network has its legitimate DHCP server, where it should get its authentic network configuration settings from. However, when there is an illegitimate DHCP server on the same local network and it is serving out a different set of network configuration settings, then the information is invalid and in most case, will lead to no connectivity to those DHCP devices. Which of the following is a term for this.
What will be an ideal response?
Name a couple of ways to vary the look of your lighting?
What will be an ideal response?
You can organize your domain into logical subgroups called ________that enable you to collect users, computers, and other resources for simplified local administration according to your company's organizational chart of departments, sections, work units, and so on
a. Sites b. Subdomains c. Organizational units d. Groups
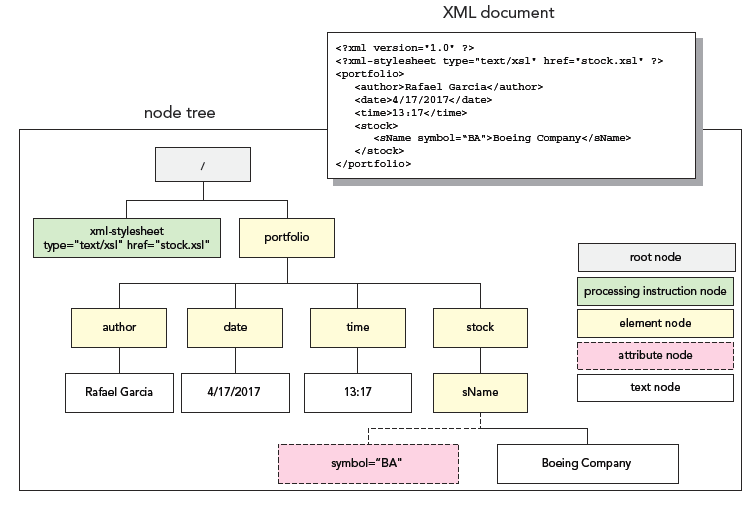
A. ?parent B. ?child C. ?sibling D. ?ancestor