If you make a mistake while recording a macro, press the ESC key and repeat the step in error.
Answer the following statement true (T) or false (F)
False
You might also like to view...
Which of the following is displayed in the cell if the value is too long to fit into a cell?
A. &&&&&&& B. *********** C. $$$$$$$$$$ D. #########
Under the SEQ global replacement strategy, when looping behavior is detected, the _________ strategy is employed.
a) least-recently-used (LRU) b) most-recently-used (MRU) c) not-used-recently (NUR) d) first-in-first-out (FIFO)
In the accompanying figure of a Microsoft Access 2016 Form Wizard dialog box, Box A points to the _____.
?
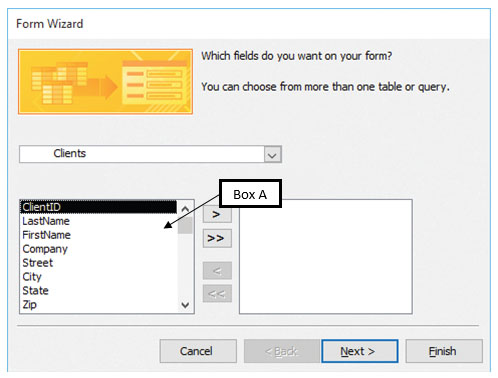
A. ?selected tables B. ?available fields C. ?selected fields D. ?available tables
External network security threats can include management failure to support organization-wide security awareness, inadequate security policies, and unenforced security procedures. _______________________
Answer the following statement true (T) or false (F)