You can create your own ____________________ for use with the fill handle.
Fill in the blank(s) with the appropriate word(s).
custom lists
You might also like to view...
RealMedia is the standard format for videos distributed on commercial DVDs.
Answer the following statement true (T) or false (F)
Destructors are automatically called whenever an object goes out of scope.
Answer the following statement true (T) or false (F)
FIGURE PPT 3-1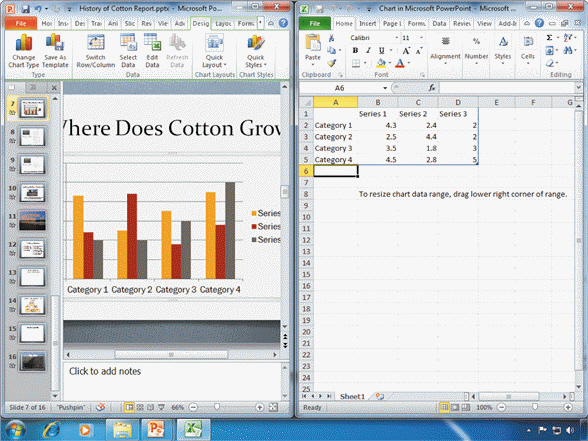 Referring to Figure PPT 3-1 above, in order to type 2005, 2006, and 2007 as column labels, you would ____.
Referring to Figure PPT 3-1 above, in order to type 2005, 2006, and 2007 as column labels, you would ____.
A. Click cell B1, type 2005, press Tab, type 2006, press Tab, press 2007 B. Click cell A1, type 2005, press Enter, type 2006, press Enter, press 2007 C. Click cell B1, type 2005, press Enter, type 2006, press Enter, press 2007 D. None of the above
Several high-level employees have recently requested remote access to corporate email and shared drives. Your company has never offered remote access. However, the company wants to improve productivity. Rapidly responding to customer demands means staff now requires remote access. Which of the following controls will BEST protect the corporate network?
A. Plan and develop security policies based on the assumption that external environments have active hostile threats. B. Implement a DLP program to log data accessed by users connecting via remote access. C. Secure remote access systems to ensure shared drives are read only and access is provided through an SSL portal. D. Implement a VLAN to allow users to remotely access internal resources.