Compromised computers attached to the Internet, which are often used to remotely perform malicious or criminal tasks, are called ________
Fill in the blank(s) with the appropriate word(s).
Answer: zombies/bots
You might also like to view...
________ to a base class may be assigned the address of a derived class object.
A) Access specifiers B) Static members C) Private members D) Pointers E) None of the above
____ controls are stand-alone compiled applications designed to make it possible to link and allow interactions between variously developed applications.?
A. ?ActiveX B. ?Applets C. ?Java widgets D. ?VBScript
Which of the following is NOT a factor to consider when running a delete query?
A) To delete records on the one side of the relationship and the related records on the many side, enable the Referential Integrity and Cascade Delete Related Records properties. B) To delete records only on the one side of the relationship, first delete the relationship, and then delete the data. C) To remove data only on the many side of the relationship, create and run the delete query without changing the relationship. D) To remove data in a many to many relationship, create and run the delete query, delete the relationship, and then delete the data.
Case Question 1Dustin is changing the navigation in the site pictured in the figure below. Rather than changing the navigation on every page, he decides to take advantage of a Dynamic Web Template.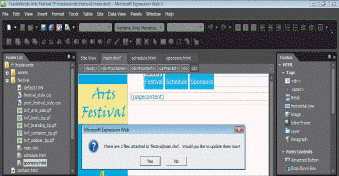
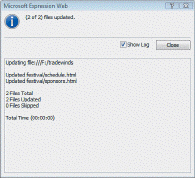 After Dustin updates the files attached to the template, he clicks the Show Log check box, as shown in the figure above. Dustin should click File on the menu bar, then click ____, so any attached files that were open in Expression Web will be saved with the changes.
After Dustin updates the files attached to the template, he clicks the Show Log check box, as shown in the figure above. Dustin should click File on the menu bar, then click ____, so any attached files that were open in Expression Web will be saved with the changes.
A. Save B. Save All C. Update D. Update All