Tethering may allow an unsecured mobile device to infect other tethered mobile devices or the corporate network.
Answer the following statement true (T) or false (F)
True
You might also like to view...
The original association rule mining formulation uses the support and confi- dence measures to prune uninteresting rules.
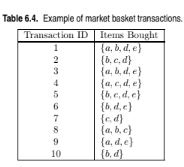
Draw a contingency table for each of the following rules using the trans-
actions shown in Table 6.4.
Rules:
![]()
Use the contingency tables in part (a) to compute and rank the rules
in decreasing order according to the following measures.
The covers come with a built-in ________ that works like a traditional mouse but uses touch
A) trackpad B) mousepad C) touchpad D) wireless pad
The diverse range of abilities needed to produce a new-media project is called the ____________________ (two words).
Fill in the blank(s) with the appropriate word(s).
Which of the following is a characteristic of AI?
A. Difficult and expensive to duplicate and disseminate knowledge B. Erratic and inconsistent total cost of knowledge C. Low creativity D. Knowledge isn't preserved well