When testing a database response, ____ characters are inserted in different places to determine vulnerability.
A. single quote
B. asterisk
C. dollar sign
D. percent sign
Answer: A
You might also like to view...
The rectangle that shows the outermost dimensions of any shape is called the:
What will be an ideal response?
In the RGB color model, white is represented by putting a(n) ________ in each RGB setting
Fill in the blank(s) with correct word
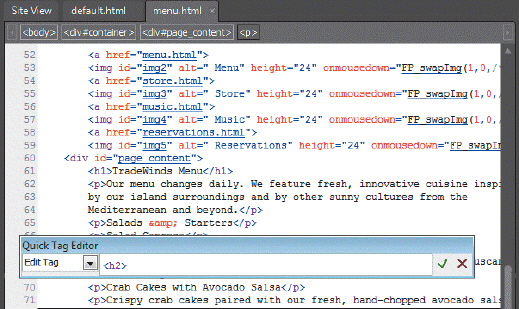 Referring to the figure above, if you clicked the green check mark (Enter button) in the Quick Tag Editor window, what would happen?
Referring to the figure above, if you clicked the green check mark (Enter button) in the Quick Tag Editor window, what would happen?
A. The opening tag would be changed to h2. B. The closing tag would be changed to h2. C. Both a and b. D. Neither a nor b.
Lisa wants to integrate with a cloud identity provider that uses OAuth 2.0, and she wants to select an appropriate authentication framework. Which of the following best suits her needs?
A. OpenID Connect B. SAML C. RADIUS D. Kerberos