If the acceptance strategy is used to handle every vulnerability in the organization, its managers may be unable to conduct proactive security activities and may portray an apathetic approach to security in general.
Answer the following statement true (T) or false (F)
True
Computer Science & Information Technology
You might also like to view...
(Challenge) you went to a video store and rented a DVD that is due in 3 days from the rental date. Input rental date, rental month and rental year. Caclculate and print return date, return month and return year.
For example,
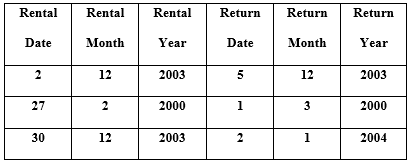
Computer Science & Information Technology
A method can return nothing, which makes it a(n) ____ method.
A. empty B. void C. open D. valid
Computer Science & Information Technology
The default font in Word is ________ and the font size is 11
A) Cambria B) Batang C) Calibri (Body) D) Arial Black
Computer Science & Information Technology
If you are not sure which chart type to pick, it may be helpful to click ________ Charts in the Chart group
Fill in the blank(s) with correct word
Computer Science & Information Technology