What security measures regarding ActiveX should you take if you are running Windows 2000 or Windows XP?
What will be an ideal response?
If you are running Windows 2000, make sure you are running Internet Explorer 6.0 and have the newest security patches in place. Then set your Internet Options security setting to High if you want no ActiveX control to be allowed, or to Medium if you wish to be informed when an ActiveX control is requesting permission for download.?If you are running Windows XP, make sure you are running IE6 or possibly IE7 (which has better security features), and set your Internet security level to at least Medium.
You might also like to view...
When an algorithm becomes more complex, the program's logic may be easier to see in ____.
A. code B. a processor C. pseudocode D. a flowchart
Case Question 2Natalie is responsible for updating her company's Web site. Her boss has asked her to choose and apply three different table styles as possible changes to existing tables. She is instructed to take screenshots of each style and bring the images to the next company meeting along with her comments and an overall recommendation.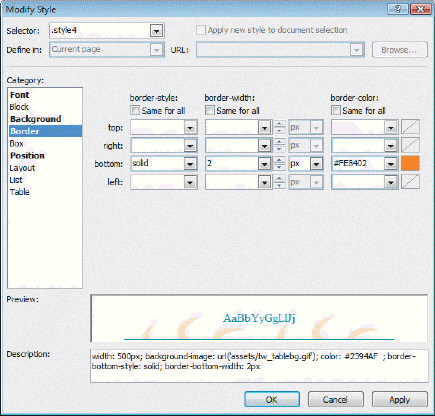 Referring to the figure above, Natalie has chosen what type of border?
Referring to the figure above, Natalie has chosen what type of border?
A. solid bottom border only for the selected cell B. solid bottom border only for the entire table C. style4 border for the entire table D. double solid bottom border only for the entire table
____ is the use of computers, video cameras, microphones, and networking technologies to conduct face-to-face meetings over a network.
A. Online conferencing B. Videoconferencing C. Phone conferencing D. VoIP conferencing
Several employees have been printing files that include personally identifiable information of customers. Auditors have raised concerns about the destruction of these hard copies after they are created, and management has decided the best way to address this concern is by preventing these files from being printed. Which of the following would be the BEST control to implement?
A. File encryption B. Printer hardening C. Clean desk policies D. Data loss prevention