Phishing is controlled by using S/MIME
Indicate whether the statement is true or false
FALSE
Computer Science & Information Technology
You might also like to view...
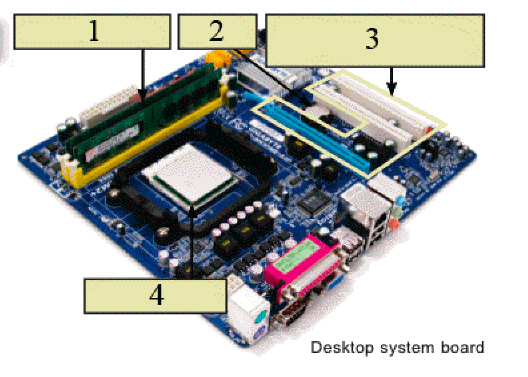 In the figure above, the object indicated by item 1 ____.
In the figure above, the object indicated by item 1 ____.
A. carries out most of the processing work that takes place in your PC B. connects your laptop keyboard to the shell C. powers your computer D. is connected to a series of RAM chips
Computer Science & Information Technology
TCP is a Network layer protocol.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
If two tables do not have a common field, Access will join the two tables by combining the records, regardless of whether they have a matching field. This is called the ________ effect
A) join B) multiplier C) relationship D) query
Computer Science & Information Technology
Usenet and Yahoo! are examples of email services
Indicate whether the statement is true or false.
Computer Science & Information Technology