Which of the following is NOT a question to be used as a self-assessment for recommended security practices in the category of people?
A. Do you perform background checks on all employees with access to sensitive data,areas, or access points?
B. Are the user accounts of former employees immediately removed on termination?
C. Would the typical employee recognize a security issue?
D. Would the typical employee know how to report a security issue to the right people?
Answer: B
You might also like to view...
To add an int value 5 to a vector v of integers, use _________.
a. v.push_back(5); b. v.add(5); c. v.append(5); d. v.insert(5);
Two phrases in the Fourth Amendment that place limitations on the government’s ability to acquire a search warrant are (select 2):
a. The Right of the People b. Redress of Grievance c. Probable Cause d. Against Unreasonable Searches
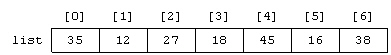 What is the minimum number of comparisons that have to be made to find 18 using a sequential search on the list shown in the accompanying figure?
What is the minimum number of comparisons that have to be made to find 18 using a sequential search on the list shown in the accompanying figure?
A. 1 B. 2 C. 3 D. 4
Arrows used in a ____ to show inheritance relationships extend from the descendant class and point to the original class.
A. method diagram B. UML diagram C. virtual method call D. composition