A _________ attack attempts to learn or make use of information from the system but does not affect system resources.
Fill in the blank(s) with the appropriate word(s).
passive
You might also like to view...
In a vector, which of the following statements is true?
a. Indexing vector access is range checked. b. The range of legal index values for a vector is 0 to the value of v.size()-1 c. To add a value use the member function v.push_front( ) d. To manage size of reserve use v.reserve(newReserve) e. To increase or decrease a vector’s size v.new_size(newSize);
Files stored in the cloud service can generally be accessed via a(n) ________ as well
Fill in the blank(s) with correct word
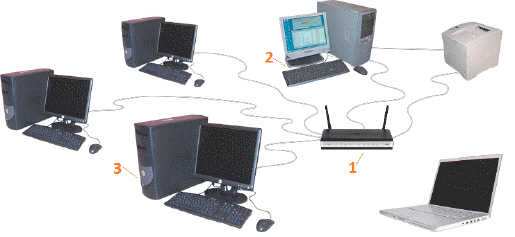 In the accompanying figure of a typical network configuration, Item 1 indicates a ____.
In the accompanying figure of a typical network configuration, Item 1 indicates a ____.
A. router B. server C. workstation D. printer
A motion clip is animated clip art.
Answer the following statement true (T) or false (F)