Which of the following is NOT among the items of information that a CVE reference reports?
A. attack signature
B. name of the vulnerability
C. description of vulnerability
D. reference in other databases
Answer: A
You might also like to view...
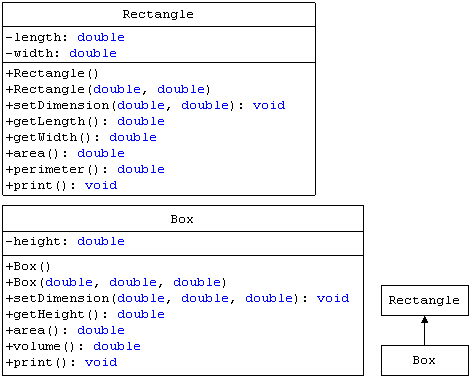 Based on the diagram in the accompanying figure, which of the following members will Box NOT have direct access to?
Based on the diagram in the accompanying figure, which of the following members will Box NOT have direct access to?
A. getHeight() B. setDimension() C. length D. print()
A Windows Application project will create a program that is designed to run using an Internet browser.
Answer the following statement true (T) or false (F)
If a value in a formula is not available, the error value #VALUE! will display in the cell.
Answer the following statement true (T) or false (F)
A(n) ____________ is a logical design that controls the order in which a set of statements execute.
a. elementary structure b. logic structure c. control structure d. sequence structure