What is the best way to protect against data loss on a stolen Windows 7 personal laptop?
A) Software piracy
B) Spyware
C) Malware
D) Adware
Answer: C) Malware
You might also like to view...
The end of a Java statement is indicated by a ________.
a. bracket (}) b. asterisk (*) c. semicolon (;) d. colon (:)
What does
ArrayList
UNIX line commands are processed by a command processor or __________ that lies between the user and the kernel.
a. interface b. IOCS c. shell d. BIOS
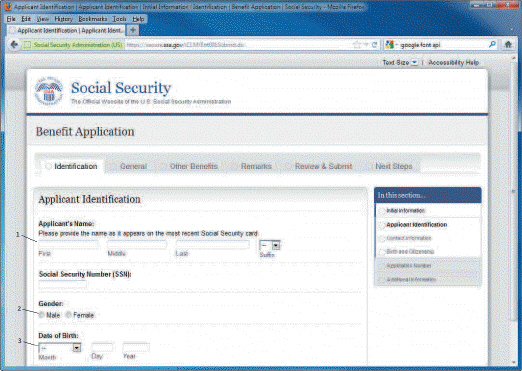 In the accompanying figure, the item labeled with the number 2 is a ____ field.
In the accompanying figure, the item labeled with the number 2 is a ____ field.
A. text box B. check box C. menu D. radio button