Advocates of ____ state that, unless individuals or businesses protect their access points, they are welcoming others to use them.
A. spoofing
B. phishing
C. spamming
D. war driving
Answer: D
Computer Science & Information Technology
You might also like to view...
The relationship between an interface and the class that implements it is
a. Composition b. Aggregation c. Inheritance d. None
Computer Science & Information Technology
________ programs are freely available for use and modification
A) Shareware B) Commercial C) Open-source D) Open standards
Computer Science & Information Technology
In Microsoft Access 2016, the Query Design button appears on the _____.?
A. ?File tab B. ?Table tab C. ?Home tab D. ?Create tab
Computer Science & Information Technology
In the accompanying figure that shows the header and footer in a Microsoft Word 2016 document, Box A points to the _____.?
?
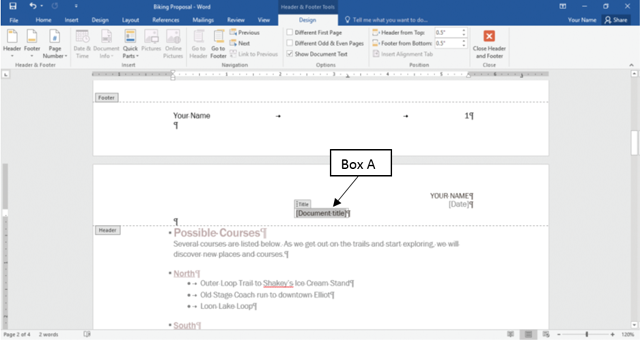
A. ?title reference marker B. ?title template C. ?title citation D. ?title content control
Computer Science & Information Technology