________ encryption is the most commonly used encryption on the Internet
Fill in the blank(s) with correct word
Public-key
You might also like to view...
Which is not a way to proceed when creating a catalog of forms to help you understand the information flow currently in use in business?
A) Collect examples of all the forms in use. B) Note the type of form. C) Document the intended distribution pattern. D) Compare the intended distribution pattern with who actually analyzes the form.
Write a class TimeOfDay that uses the exception classes defined in the previous exercise. Give it a method setTimeTo(timeString) that changes the time if timeString corresponds to a valid time of day. If not, it should throw an exception of the appropriate type.
What will be an ideal response?
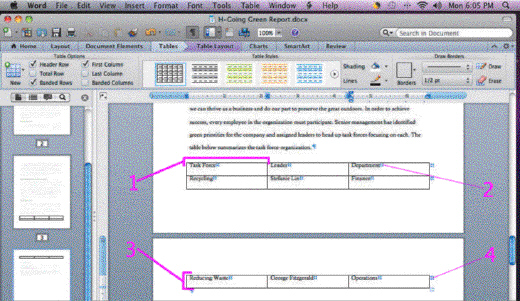 In the accompanying figure, Item 1 points to a ____.
In the accompanying figure, Item 1 points to a ____.
A. row B. column C. tab D. thumbnail
When creating a chart, best practices indicate that you first consider ________
A) how quickly it needs to be created B) who will be viewing the chart C) the basic design of the chart D) the data