The ____ model is used as a "bridge" solution in situations where WPA or WPA2 security is not available.
A. personal security
B. enterprise security
C. SOHO security
D. transitional security
Answer: D
Computer Science & Information Technology
You might also like to view...
How do you insert a regular tab character within a cell?
A) Shift+Tab B) Ctrl+Tab C) Ctrl+left arrow D) F12
Computer Science & Information Technology
To move quickly between comments, click the ________ button
A) Show Markup B) Down C) Move D) Next
Computer Science & Information Technology
What is the function of UVs?
A. They change the position of vertices in the mesh. B. They make the model look better. C. They define how an image will be projected onto a surface. D. They are useful to show how the model would be constructed from a flat surface.
Computer Science & Information Technology
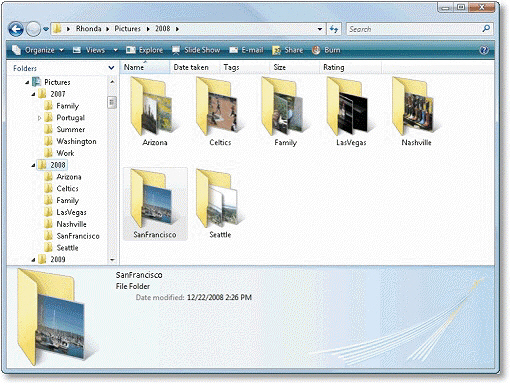 In the accompanying figure, pictures from a visit to a basketball game were stored in a folder named ____.
In the accompanying figure, pictures from a visit to a basketball game were stored in a folder named ____.
A. San Francisco B. Arizona C. Family D. Celtics
Computer Science & Information Technology