Match the following terms with their appropriate description.
A. Tunneling communication protocol that enables IPv6 connectivity between IPv6/IPv4 nodes across network address translation (NAT) interfaces
B. Address that enables the delivery of packets to each of multiple interfaces
C. An IPv6 address represented in the form 0:0:0:0:0:0:w.x.y.z, where w.x.y.z is the IPv4 address in dotted-decimal
D. An IPv4-only node is represented as :ffff:.w.x.y.z to an IPv6 node and used only for internal representation
E. Address that is utilized only for a destination address assigned to a router
F. Type of IPv6 address used for communication between neighboring nodes on the same link, and equivalent to IPv4 addresses configured using APIPA
G. The dynamic IPv4 addressing system used when DHCP is unavailable
1. IPv4-compatible address
2. IPv4-mapped address
3. Link local IPv6 address
4. Teredo
5. Multicast IPv6 address
6. Anycast IPv6 address
7. Automatic Private IP Addressing (APIPA)
Answer:
A. 4.
B. 5
C. 1
D. 2
E. 6
F. 3
G. 7
You might also like to view...
A ________ determines whether a field contains an integer value in an acceptable range.
a. f:validateDoubleRange. b. f:validateLength. c. f:validateLongRange. d. None of the above.
Write down the command to compile a C++ program in the myLab1.C file and store the executable code in the file myLab1. The C++ program uses functions in the math library and the PROMPT macro as shown below. The macro definition is not written at the start of the program.
The following command can accomplish the given task. Note that the command is to be typed as one line and that the line break is due to smaller line length.
?In the accompanying figure of a PowerPoint 2016 presentation, box _____ is pointing to the Decrease Font Size button.
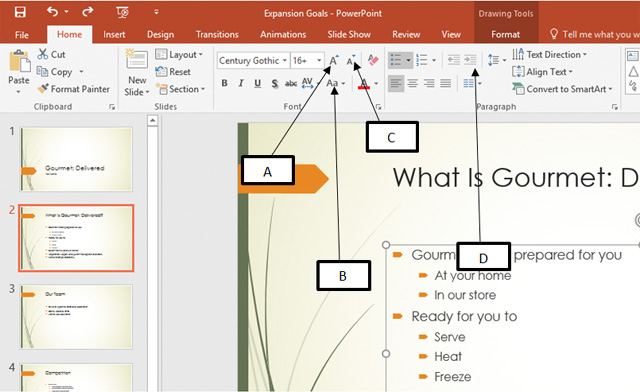
A. ?C B. ?B C. ?D D. ?A
A(n) ____________________ IDS watches for suspicious behavior on systems, thus it is a behavior based IDS.
Fill in the blank(s) with the appropriate word(s).