What is used to create session keys?
A. master secret
B. crypto modules
C. validation
D. domain validation
Answer: A
Computer Science & Information Technology
You might also like to view...
Loops that terminate upon reading a unique input value are called
What will be an ideal response?
Computer Science & Information Technology
Grouped records combine records with identical values from a report field
Indicate whether the statement is true or false
Computer Science & Information Technology
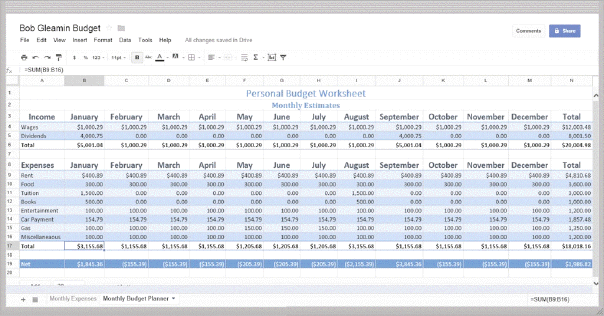
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
Which of the following defines an IP address that is NOT routed on the Internet?
A. Multicast B. Public C. Private D. Classful
Computer Science & Information Technology