If a blogger posts an entry about a current event, a ________ might post a comment with a claim of new information about that event by posting a link to a malicious website designed to take advantage of users who do not have updated security
A) scammer B) blog owner C) spammer D) spimmer
A
Computer Science & Information Technology
You might also like to view...
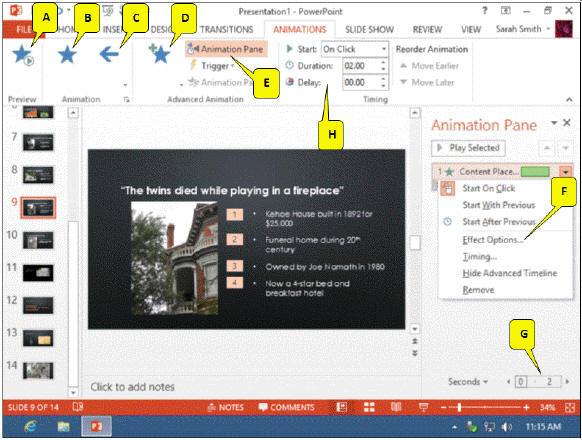 Referring to the accompanying figure, which callout points to the option used to customize the animation?
Referring to the accompanying figure, which callout points to the option used to customize the animation?
A. D B. E C. F D. G
Computer Science & Information Technology
Would disk scheduling be useful for a single-user, dedicated disk in a sequential file processing application?Why?
What will be an ideal response?
Computer Science & Information Technology
When you draw a hierarchy chart, you use more of a "____" approach.
A. big picture B. small picture C. detail-oriented D. focused view
Computer Science & Information Technology
Which of the following is NOT an Excel add-in program?
A. Analysis ToolPak B. Solver C. What If D. All are Excel add-in programs.
Computer Science & Information Technology