In ________, Excel maximizes the number of cells visible on the screen
A) Page Layout view B) Backstage view C) Chart styles D) Normal view
D
Computer Science & Information Technology
You might also like to view...
What type of ICMP packet can an attacker use to send traffic to a computer they control outside the protected network?
A. Source Quench B. Echo Request C. Destination Unreachable D. Redirect
Computer Science & Information Technology
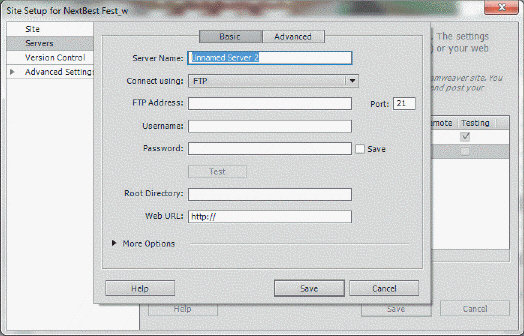 The dialog box in the accompanying figure is used to fill in the values provided by your ____.
The dialog box in the accompanying figure is used to fill in the values provided by your ____.
A. ASP B. OSP C. ISP D. none of the above
Computer Science & Information Technology
?A common field is an attribute that appears in only one entity.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
The Border button is located on the ____ tab.
A. PAGE LAYOUT B. INSERT C. HOME D. DESIGN
Computer Science & Information Technology