An application program transparently requests operating system services through __________.
a. a command language
b. the IOCS
c. the file system
d. an application programming interface (API)
d. an application programming interface (API)
You might also like to view...
Write two paragraphs that compare and contrast the process of app development and the S D L C
What will be an ideal response?
Consider six transactions T 1 , T 2 , T 3 , T 4 , and T 5 with:
T 1 initiated at site S 1 and spawning an agent at site S 2 ,
T 2 initiated at site S 3 and spawning an agent at site S 1 ,
T 3 initiated at site S 1 and spawning an agent at site S 3 ,
T 4 initiated at site S 2 and spawning an agent at site S 3 ,
T 5 initiated at site S 3 .
The locking information for these transactions is shown in following table.
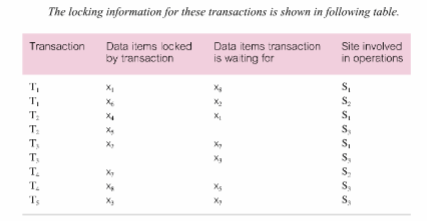
(a) Produce the local wait-for-graphs (WFGs) for each of the sites. What can you conclude from the local WFGs?
(b) Using the above transactions, demonstrate how Obermarck’s method for distributed deadlock detection works. What can you conclude from the global WFG?
To save a document as a template that can be reused when needed, use the following path:
A. File/New B. File/Save As C. Home/Styles/Change Styles D. Insert/Text/Quick Parts
A folder target in a DFS namespace is in what format?
A. Universal Naming Convention (UNC) format B. User@Domain/location format C. File Hierarchical format D. B-Tree Organized format