Programs that do not follow the rules of structured logic are ____ programs.
A. structured
B. scrambled
C. unstructured
D. disorganized
Answer: C
Computer Science & Information Technology
You might also like to view...
Few designers create a reset style sheet to define their default styles.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
What can an attacker use a port scanner to test for on a target computer?
A. invalid IP addresses B. SYN flags C. open sockets D. ping floods
Computer Science & Information Technology
During the _________________________, your customer must enter applicable name, address, and payment information.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
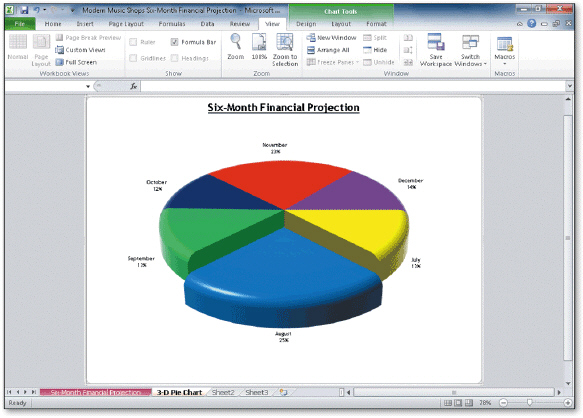 Using the accompanying figure, identify the following chart elements: chart sheet, chart title, Pie chart, data series, category names, exploded slice, and data labels.
Using the accompanying figure, identify the following chart elements: chart sheet, chart title, Pie chart, data series, category names, exploded slice, and data labels.
What will be an ideal response?
Computer Science & Information Technology