A form that is fully read-only permits you to:
What will be an ideal response?
view records.
Computer Science & Information Technology
You might also like to view...
The principal objective for developing a _________ is to enable secure, convenient and efficient acquisition of public keys.
A. KDC B. IETF C. PKI D. CRL
Computer Science & Information Technology
Which of the following is not a control structure?
a. sequence b. selection c. syntax d. repetition
Computer Science & Information Technology
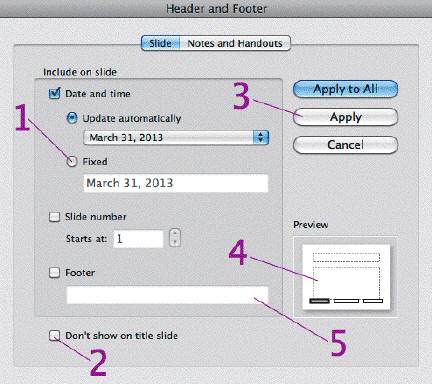 In the accompanying figure, Item 5 points to the ____.
In the accompanying figure, Item 5 points to the ____.
A. Header text box B. Slide text box C. Footer text box D. Title text box
Computer Science & Information Technology
Many companies are extending internal enterprise resource planning (ERP) systems to their suppliers and customers, using a concept called _____.?
A. ?supply chain management (SCM) B. ?stand-alone computing C. cloud computing D. ?behavioral management
Computer Science & Information Technology