Which of the following protocols does PPTP use for authentication?
A) EAP and L2TP
B) EAP and PPP
C) EAP and IPSec
D) EAP and CHAP
D) EAP and CHAP
You might also like to view...
Write the pseudocode for below problem
Compute the average grade on a quiz for a class of any number of students.
Internet Explorer protected mode helps protect against which computer threat?
A) virus infections B) malware being installed on your computer C) hackers seeing your personal data D) unauthorized user logon
____ provide filtering and network traffic control on LANs and WANs. These devices can connect multiple segments and multiple networks.
A. Hubs B. Routers C. Switches D. Bridges
Answer the following statement(s) true (T) or false (F)
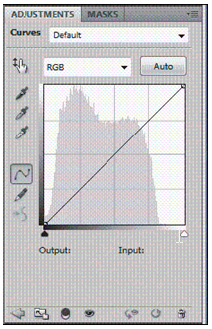
1. The values of Output tones are represented horizontally in the accompanying figure. _________________________
2. The values of Input tones are represented horizontally in the accompanying figure. _________________________
3. To remove a color marker, select the Color Sampler Tool, place the pointer over the color marker, and Alt-click the marker to delete it. _________________________
4.When you can use the Healing or Spot Healing Brush Tool on a blank layer above the layer you would like to affect, the adjustments are destructive. _________________________