In information security, a specification of a model to be followed during the design, selection, and initial and ongoing implementation of all subsequent security controls is known as a __________.
A. framework
B. security plan
C. security standard
D. blueprint
Answer: A
You might also like to view...
A customer wants a report to show the total sales for each salesman in the district, a total of sales for each district in the sales region and the totals sales in each region for the company. You correctly identify this as:
a. A detail report b. A summary report c. An exception report. d. A break report. e. b and d.
Analyze the following code:
``` public class Test { public static void main(String[] args) { new B(); } } class A { int i = 7; public A() { System.out.println("i from A is " + i); } public void setI(int i) { this.i = 2 * i; } } class B extends A { public B() { setI(20); // System.out.println("i from B is " + i); } @Override public void setI(int i) { this.i = 3 * i; } } ``` a. The constructor of class A is not called. b. The constructor of class A is called and it displays "i from A is 7". c. The constructor of class A is called and it displays "i from A is 40". d. The constructor of class A is called and it displays "i from A is 60".
Activate the NAT on the Customer router’s interfaces. This requires that you activate NAT on the FA0/0 and S0/0/0 interfaces. Carefully select whether to use ip nat inside or ip nat outside on each interface. List the router prompt and the command used to complete this task.
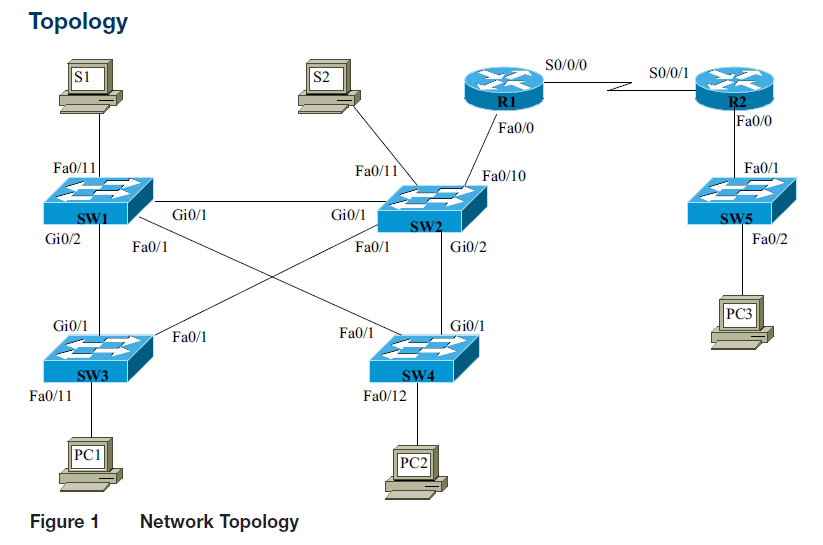
What will be an ideal response?
The ________ button enables you to change brightness, contrast, or sharpness of a picture
Fill in the blank(s) with correct word