Malware that collects personal information or displays advertisements is called:
A) shareware B) spyware C) patch software D) freeware
B
You might also like to view...
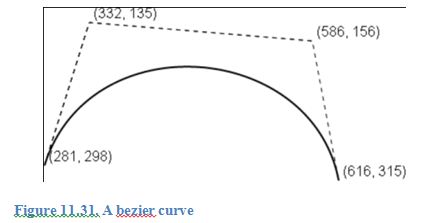
Figure 11.31 shows a bezier curve with start, end, and control points. Fill in the blanks to complete the statements for drawing this bezier curve. Assume the curve is drawn on a canvas with a rendering context, myContext.
1. myContext.___(___, ___);
2. myContext.___(___,___,___,___,___,___);
Which of the following allows you to choose alternative file formats when you save a file?
A. Save as type B. Save as format C. Save with extension D. Save as document
apply a style to exactly one element on a web page, configure a CSS _____________.
a. group b. id c. class d. None of the above
Write a subquery that finds average salary by each department. Check to find if employee 543’s salary satisfies =ANY,
Use the N2 Corporation database tables to design the following subqueries. (Use the spooling method to capture all queries and results in the CHAP8SP1.LST file.)