Which of the following is not an example of good cloud security?
A. Strong data access policies
B. Powerful authentication methods
C. Eight-character passwords
D. Encryption
C. Eight-character passwords are not an example of good cloud security. Ten or higher character passwords are the preferred method.
You might also like to view...
Briefly describe the two types of virtual desktops that Remote Desktop Services can provide.
What will be an ideal response?
A cluster disk with a status of Redirected Access means that access to the volume is temporary unavailable.
Answer the following statement true (T) or false (F)
When you install an ISDN terminal adapter (TA), what special number provided by the telephone company must be configured along with the other ISDN telephone number you want to call?
A. Default gateway B. Service Profile ID (SPID) C. DS0 D. Basic Service Set Identifier (BSID)
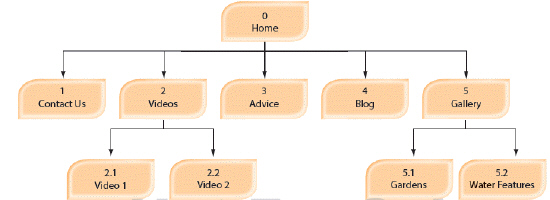 What is the accompanying figure an example of?
What is the accompanying figure an example of?
A. timeline B. wireframe C. deliverables D. resources