Consider a class that uses the following variables to implement an array-based stack:
```
String [] s = new String[100];
int top = 0;
```
a method that implements the String peek() operation can be written as
A) return s[top];
B)
if (top == 0)
throw new RuntimeException("Underflow");
else
return s[top];
C)
if (top == 0)
throw new RuntimeException("Underflow");
else
return s[top-1];
D) return s[top-1];
C)
if (top == 0)
throw new RuntimeException("Underflow");
else
return s[top-1];
You might also like to view...
Given the list elements and contents below. Which type of list collection could be used to represent them? Explain your choice.
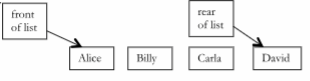
What will be an ideal response?
What data structure is used with chaining?
a. Linked list b. Queue c. Stack d. Data dictionary
The function used to overload the ostream insertion operator is referred to as a(n) ____.
a. user-defined function b. static function c. friend function d. operator function
What does the following command accomplish? nc –v –z –w 1 10.10.23.4 1-1024
a. Starts a listener on the hacker's machine b. Port scans the following IP address 10.10.23.4 c. Blocks traffic to the following IP address 10.10.23.4 d. Allows all traffic to the following IP address 10.10.23.4