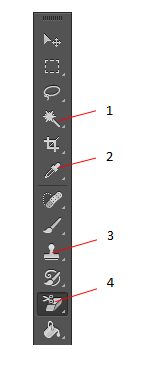
In the figure above, the number 2 refers to the ____________________ tool.
Fill in the blank(s) with the appropriate word(s).
Eyedropper
You might also like to view...
What type of loop always performs the loop statements at least once?
What will be an ideal response?
Terrorists who turn their attacks to the network and computer infrastructure to cause panic among citizens are known as which of the following?
A. cyberterrorists B. spies C. hackers D. hacktivists
When using a wildcard in a query criteria, a user should substitute a(n) ________ for the missing unknown character(s)
A) quotation marks (") B) asterisks (*) C) pound signs (#) D) ampersands (&)
?Suppose you have an accounting background and you are considered an expert in the field of discovering errors in electronic spreadsheets. You are considered a knowledge engineer if you are part of a team that is developing an expert system to discover errors in spreadsheets. .
Answer the following statement true (T) or false (F)