?A security ?monitor is a conceptual piece of the system within the trusted computer base that manages access controls-in other words, it mediates all access to objects by subjects. __________
Answer the following statement true (T) or false (F)
False
You might also like to view...
Given the linked list below, and if the data field of the above nodes is called data and the pointer field is called link, which of the following is not a correct way to reference the data field of node C.
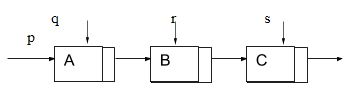
a) s->data
b) r->link->data
c) q->link->link->data
d) p->link->link->link->data
On any ____________________ channel thumbnail, the masked part of the image is black, indicating that it is protected.
Fill in the blank(s) with the appropriate word(s).
How would you identify entity and relationship types from a user’s requirements specification?
What will be an ideal response?
As in algebra, you can use brackets to override the order of operations Excel follows to perform formula calculations.
Answer the following statement true (T) or false (F)