Corporations and end users who want to access data, programs, and storage from anywhere that there is an Internet connection should use _________
Fill in the blank(s) with the appropriate word(s).
Cloud computing
You might also like to view...
Which of the following is not true about protecting your electronic profile?
A) Every time you provide information to a company, that company may enter the information into a database. B) If nothing else, your name, address, and telephone number are available online for others to see. C) One way to keep yourself safe is to set up an alternate e-mail that you only use when you sign up for promotions or website access. D) Filling out forms online gives the recipient more information than you intend.
What are two basic rules of troubleshooting (one is similar to the Hippocratic Oath)?
What will be an ideal response?
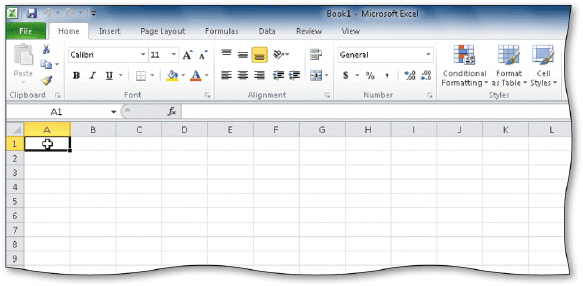 A thin red border indicates the active cell, as shown in the accompanying figure.
A thin red border indicates the active cell, as shown in the accompanying figure.
Answer the following statement true (T) or false (F)
A __________ is a router or special purpose computer that examines packets flowing into and out of a network and restricts access to the organization's network
a. firewall b. token system c. ANI d. call-back modem e. firefighter