A ___________________ that is installed on a computer allows the attacker to return at a later time and bypass security settings.
Fill in the blank(s) with the appropriate word(s).
backdoor
You might also like to view...
You are required to create a conceptual data model of the data requirements for a company that specializes in IT training. The Company has 30 instructors and can handle up to 100 trainees per training session. The Company offers five advanced technology courses, each of which is taught by a teaching team of two or more instructors. Each instructor is assigned to a maximum of two teaching teams or may be assigned to do research. Each trainee undertakes one advanced technology course per training session.
(a) Identify the main entity types for the company. (b) Identify the main relationship types and specify the multiplicity for each relationship. State any assumptions you make about the data. (c) Using your answers for (a) and (b), draw a single ER diagram to represent the data requirements for the company.
In practice, most real-life applications using linked lists require a user-defined object consisting of a combination of data types.
Answer the following statement true (T) or false (F)
FIGURE AC 5-1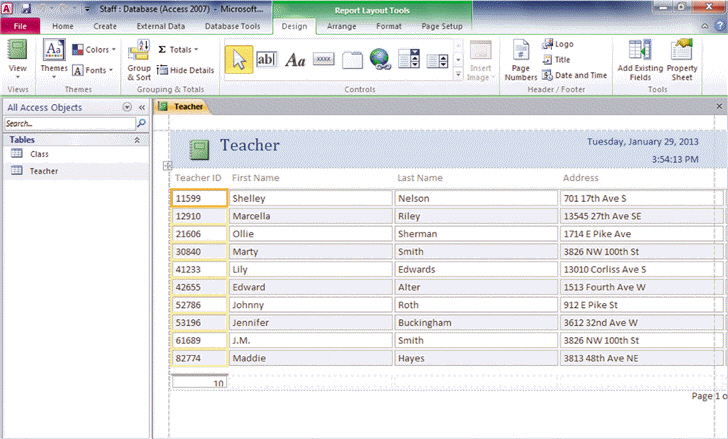 Referring to the figure above, in this report, ____ appear in controls.
Referring to the figure above, in this report, ____ appear in controls.
A. the Teacher ID label B. the records shown below the Teacher ID label C. both a. and b. D. neither a. nor b.
When designing and building a network, what are the seven categories to consider?
What will be an ideal response?