You can add extra functionality to PowerPoint presentations by using prebuilt programs called ________ controls
Fill in the blank(s) with correct word
ActiveX
You might also like to view...
An int greater than 1 is said to be prime if it is divisi- ble by only 1 and itself. For example, 2, 3, 5 and 7 are prime numbers, but 4, 6, 8 and 9 are not. Write an application that takes two numbers (representing a lower bound and an upper bound) and determines all of the prime numbers within the specified bounds, inclusive. Your application should appear as in Fig. 12.32.
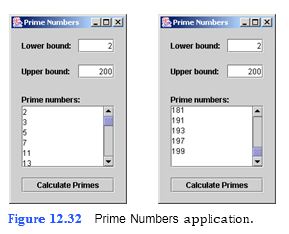
a) Copying the template to your working directory. Copy the C:Examples Tutorial12ExercisesPrimeNumbers directory to your C:SimplyJava directory.
b) Opening the template file. Open the PrimeNumbers.java file in your text editor.
c) Adding a method to determine if a number is prime. On line 154, add a comment indicating that the method will determine if a number is a prime number. On line 155, add the method header for this method. The method will be called isPrime. This method returns a value of type boolean and takes an argument of type int. Name the parameter number. On line 156, add a left brace to begin the body of the method. On line 158, add the right brace to end the body of the method. Follow the brace with a comment indicating the end of this method. You will add functionality to this method in the next step.
d) Dealing with the number 1. The number 1 is not a prime number. On line 157, add a comment stating that 1 is not a valid prime number. On line 158, add an if statement t
Which of the following is NOT true regarding linked tables?
A) When data are shared among many databases and is stored in a central location on a computer network, Access provides the ability to link to the data. B) A linked table provides a link to data stored in another database or application. C) Linking tables can increase data redundancy. D) Access can link to a table in another Access database, an Excel spreadsheet, or to tables in SQL and Oracle databases.
_____________ agnostic means that the content should be accessible and attractive regardless of the mobile operating system.
Fill in the blank(s) with the appropriate word(s).
Sara, a security administrator, sends an email to the user to verify their password has been reset. Which of the following threats is BEST mitigated by this action?
A. Spear phishing B. Impersonation C. Hoaxes D. Evil twin