____ is a form of social engineering, characterized by attempts to fraudulently acquire sensitive information by posing as a trustworthy person or business in an apparently official electronic communication.
A. Cross-site scripting
B. Denial of service
C. Phishing
D. SQL injection
Answer: C
Computer Science & Information Technology
You might also like to view...
On switch SW4, ping switch SW5 and PC3. What are the results? And why?
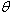
What will be an ideal response?
Computer Science & Information Technology
A nested IF requires one or more IF functions joined by an AND function
Indicate whether the statement is true or false.
Computer Science & Information Technology
A Microsoft technology that enables employees in an organization to access information across organizational and geographic boundaries.
A. Hangouts B. LMS C. SharePoint
Computer Science & Information Technology
Which of the following is NOT an antivirus software?
A. Connection Doctor B. McAfee C. Norton D. XProtect
Computer Science & Information Technology