What should you be armed with to adequately assess potential weaknesses in each information asset?
A. properly classified inventory
B. audited accounting spreadsheet
C. intellectual property assessment
D. list of known threats
Answer: A
You might also like to view...
The criteria used in the design of the __________ focused on the design of the S-boxes and on the P function that takes the output of the S-boxes.
A) ?Avalanche Attack B) ?Data Encryption Standard C) ?Product Cipher ? D) ?Substitution Key
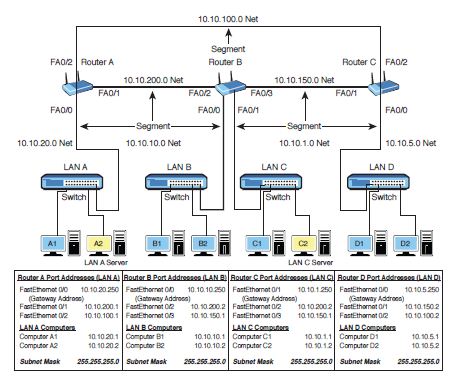
What is the next hop address for the FastEthernet port 2 on Router C in Figure 8-12?
Figure 8-12
How would you determine the longer name for the l (lowercase “el”) LDAP object class?
What will be an ideal response?
?Case 1-1Casey is learning about the types of servers and more powerful computers available. She has asked her friend Burt, an expert on computers and its uses, to quiz her.Burt describes an incredibly expensive computer designed to focus all of its computing power on one specific task at a time that can handle applications requiring speed, accuracy, and processing capabilities. Casey identifies the type of computer to be a(n) _____.
A. ?wireframe computer B. ?supercomputer C. ?mainframe computer D. ?enterprise-class computer