Bryan has a set of sensitive documents that he would like to protect from public disclosure. He would like to use a control that, if the documents appear in a public forum, may be used to trace the leak back to the person who was originally given the document copy. What security control would best fulfill this purpose?
A. Digital signature
B. Document staining
C. Hashing
D. Watermarking
Answer; D. Watermarking
You might also like to view...
How many times is the loop body of the for statement executed?
Assume that all variables are of type int and that y and z are initialized to 0. ``` for (int i = 0; i < 100; ++i) { cin >> x; y += x; if ( x % 2 == 0 ) ++z; } ``` a. once b. 99 times c. 100 times d. until a number larger than 100 is entered
Which of the following provides the BEST solution for customers needing quiet cooling options?
A. Side panel slots B. Liquid based C. Additional fans D. Thermal paste
For a fantasy wargame that you have been playing, you want to change the U.S. flag for the flag for a fictional country for which you are battling. If you want to erase all the red pixels on the stripes in the flag with one tap or click, what is the best tool to use? a.Eraser Toolc.Magic Eraser Toolb.Background Eraser Toold.Color Eraser Tool
What will be an ideal response?
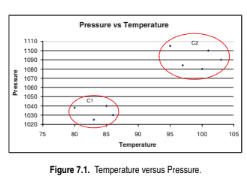
How many natural clusters do you observe from the graph? Assign a label (C1, C2, etc.) to each cluster in the graph.