Arranging data in a table from A to Z is referred to as ________
Fill in the blank(s) with correct word
sorting
Computer Science & Information Technology
You might also like to view...
In each example, when would you use a hash and when would you use an array?
a. Counting the number of occurrences of an IP address in a log file. b. Generating a list of users who are over disk quota for use in a report.
Computer Science & Information Technology
Which VPN protocol uses UDP port 1701 and does not provide confidentiality and authentication?
A. IPsec B. L2TP C. PPTP D. SSL
Computer Science & Information Technology
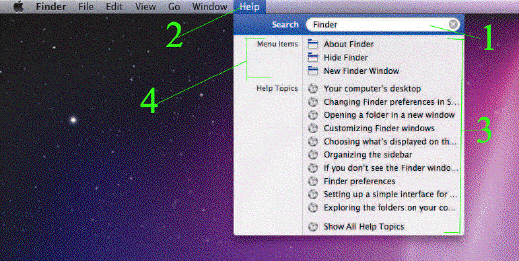 In the accompanying figure, Item 3 points to the ____.
In the accompanying figure, Item 3 points to the ____.
A. Help menu B. Search field C. Search results list D. Menu items section
Computer Science & Information Technology
Which of the following is FALSE about the NOW function?
A) It uses military time. B) It displays the current date and time. C) It uses the computer's clock to display the date and time. D) It displays the current date in a cell.
Computer Science & Information Technology