Authentication in JAAS is performed in a pluggable and stackable fashion. It is based on a concept called the ___________________ framework.
Fill in the blank(s) with the appropriate word(s).
PAM (pluggable authentication module)
Computer Science & Information Technology
You might also like to view...
A standard monitor has an on-screen show ratio of ____.
A. 3:4 B. 1:2 C. 16:9 D. 4:3
Computer Science & Information Technology
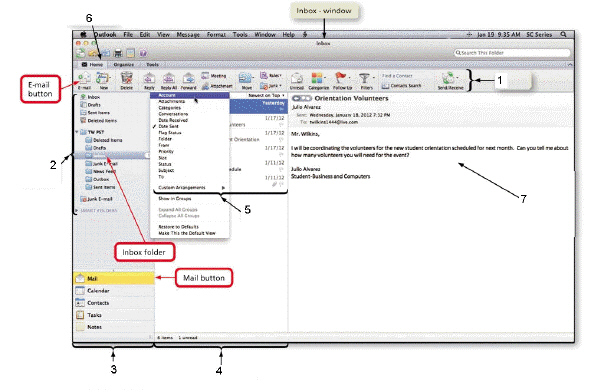 The item numbered 7 in the accompanying figure is the ____.
The item numbered 7 in the accompanying figure is the ____.
A. Mail folder B. Navigation Pane C. message pane D. Reading Pane
Computer Science & Information Technology
A kiosk presentation loops continually with no need for a presenter
Indicate whether the statement is true or false
Computer Science & Information Technology
____________________ is the science of "secret writing."
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology