The ____ approach to network security entails a partitioned or subdivided topology.
A. segmented
B. hub
C. spoke
D. ring
Answer: A
Computer Science & Information Technology
You might also like to view...
A small text file that contains your personal information, such as preferences, that is put on your computer by a Web site is called a(n):
A) script B) cookie C) thread D) post
Computer Science & Information Technology
When editing a subdocument, only the subdocument is modified
Indicate whether the statement is true or false
Computer Science & Information Technology
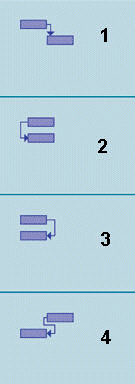 The item marked 3 in the accompanying figure is a ____ task dependency.
The item marked 3 in the accompanying figure is a ____ task dependency.
A. Finish-to-Finish B. Start-to-Finish C. Finish-to-Start D. Start-to-Start
Computer Science & Information Technology
Regarding flagged errors, use of the passive voice is identified as a grammar error
Indicate whether the statement is true or false
Computer Science & Information Technology