__________ refers to the physical components that a computer is made of.
a. Input
b. Main memory
c. Control unit
d. Hardware
d. Hardware
You might also like to view...
Microsoft Office Online web apps are NOT full-featured versions of the Microsoft Office applications
Indicate whether the statement is true or false
(Inventory Application Enhancement) Enhance the Inventory application to include a JTextField in which the user can enter the number of shipments received in a week (Fig. 4.11). Assume every shipment has the same number of cartons (each of which has the same number of items), and modify the code so that the Inventory application uses the num- ber of shipments in its calculation.
a) Copying the template to your working directory. Copy the C:Examples Tutorial04ExercisesInventory2Enhancement directory to your C:Simply- Java directory.
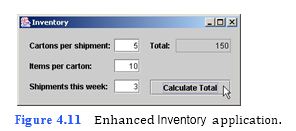
b) Opening the Command Prompt window and changing directories. Open the Com- mand Prompt window by selecting Start > Programs > Accessories > Command Prompt. Change to your working directory by typing cd C:SimplyJava Inventory2Enhancement.
c) Compiling the template application. Compile your application by typing javac Inventory.java.
d) Running the template application. Run the enhanced Inventory template applica- tion by typing java Inventory. The GUI of the Address Book template application should appear as shown in Fig. 4.12. Note the differences from Fig. 4.11.
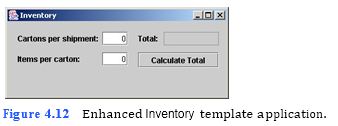
e) Opening the template file. Open the Inventory.java file in y
An application-specific evaluation is designed to enable evaluators to __________.
a) determine which applications a system executes the best b) determine which system will execute an application (or group of applications) the best, regardless of how well the system executes other tasks c) compare the overall performance of two different systems d) both a and c
Guidelines to follow when determining data entry and storage considerations include all of the following
A. data should be entered into the system where and when it occurs B. data should be verified when it is entered C. data duplication should be encouraged D. data should be entered into a system only once