Which one of the following is a disadvantage of placing security within IT?
A. It is attractive because security and IT possess many of the same qualities and technological skills
B. Security has no independence from IT and it is hard to blow the whistle on security issues occurring within the IT department or by the CIO
C. The centralizing of security and IT under the CIO
D. The CIO would have IT implement security and is likely to back the security department in its effort to create a strong and safe information system for the organization
B. Security has no independence from IT and it is hard to blow the whistle on security issues occurring within the IT department or by the CIO
You might also like to view...
Answer the following statements true (T) or false (F)
1) GroupBoxes have a text display and can have scrollbars inserted into them. 2) Panels have the ability to have scrollbars should their contents get too big. 3) The AutoScroll property will cause a Panel to scroll to the bottom if the controls displayed are too large. 4) GroupBoxes can display captions and do not include scrollbars, whereas Panels can include scrollbars and do no include a caption.
The relation shown in Figure 15.12 describes hospitals (hospitalName) that require certain items (itemDescription), which are supplied by suppliers (supplierNo) to the hospitals (hospitalName). Furthermore, whenever a hospital (h) requires a certain item (i) and a supplier (s) supplies that item (i) and the supplier (s) already supplies at least one item to that hospital (h), then the supplier (s) will also be supplying the required item (i) to the hospital (h). In this example, assume that a description of an item (itemDescription) uniquely identifies each type of item.
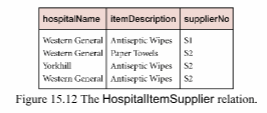
(a) Describe why the relation shown in Figure 15.12 is not in 5NF.
(b) Describe and illustrate the process of normalizing the relation shown in Figure 15.12 to 5NF.
How can you add emphasis to a form or report?
What will be an ideal response?
The main mechanism for providing access to a database is the ____ command.
A. PERMIT B. ACCESS C. GRANT D. REVOKE