Upon inspecting sniffer traffic, Jane, a technician, observes an entry that originates from port TCP 53422 with a destination of TCP 22. Which of the following protocols is MOST likely in use?
A. HTTP
B. HTTPS
C. SSH
D. DNS
Answer: C. SSH
You might also like to view...
Answer the following statements true (T) or false (F)
1. When the properties in the Properties window are displayed alphabetically, the (name) property appears at the bottom of the list. 2. To add a control to a form, you find it in the Toolbox and then double-click it. 3. You cannot click and drag controls from the Toolbox onto a form. 4. Once a control has been added to a form, it cannot be deleted.
When viewing a presentation in Slide Master view, the slide master is the larger, top slide thumbnail shown in the left pane that coordinates with the Title and Content Layout
Indicate whether the statement is true or false
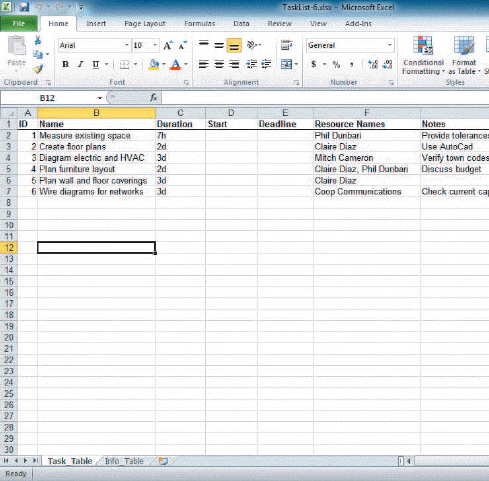 Excel column heads in Row 1 map to ____________________.
Excel column heads in Row 1 map to ____________________.
Fill in the blank(s) with the appropriate word(s).
Working with others is also known as ________
Fill in the blank(s) with correct word