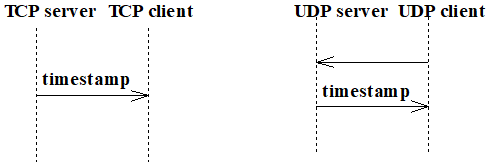
10. Draw a sequence diagram for the daytime protocol.
What will be an ideal response?
You might also like to view...
A(n) ____ story is a prose description of what software is to do, from the perspective of a person using the software.
A. objective B. user C. short D. viewer
Which of the following method calls would not be valid with the following method header?
Sub Example(ByVal a As Boolean, Optional ByVal value2 As Integer = 0) a) Example() b) Example(True) c) Example(False, 10) d) None of the above
In the real world, you'll save the vast majority of your files as basic PSD documents
Answer the following statement true (T) or false (F)
An attack that takes place shortly after a security hole is publicized, with no downloadable patch available, is called a(n):
A) zero-time exploit B) zero-patch exploit C) zero-hour exploit D) zero-day exploit