Trying to push an element into an empty stack leads to an error condition.
Answer the following statement true (T) or false (F)
False
Correct.
You might also like to view...
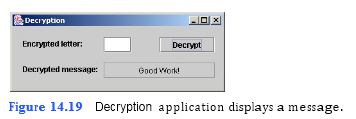
Develop an application that allows a user to decrypt a secret message (a string of numbers). The user should enter each number of the message one at a time in a JTextField. When the Decrypt JButton is clicked, the number should be decrypted to a letter. That letter should then be appended to the Decrypted message: JTextField. When the user enters the numbers 39, 79, 79, 68, 0, 55, 79, 82, 75, 1 in order, your application should appear as in Fig. 14.19.
a) Copying the template to your working directory. Copy the C:Exam- plesTutorial14ExercisesDecryption directory to your C:SimplyJava direc- tory.
b) Opening the template file. Open the Decryption.java file in your text editor.
c) Adding an instance variable. After the last GUI component is declared (line 18), add a declaration for a private String named message which will hold the decrypted message. Initialize message to the empty string. Use one line for a com- ment.
d) Storing the user input. Add code in the decryptJButtonActionPerformed method that will store the user input in an int variable named encryptedLetter. The rest of the code you will add in this exercises should be placed in the decryptJButtonAc- tionPerformed method.
e) Testing the user input. Your application should only accept user input in the range 0 to 94. Add an if statement that will test whether the user’s input is in the accepted range of values.
f) Decrypting the input. Add
One early safeguard to protect your purchases and your anonymity was called ____________________, a protocol developed by Netscape for transmitting private documents securely over the Internet.
Fill in the blank(s) with the appropriate word(s).
Network _________ enables a computer to see other devices on a network and determines whether that computer can be seen by others.
Fill in the blank(s) with the appropriate word(s).
The writing style you are most likely to use in a business class is:
What will be an ideal response?