Before you run a password cracking program on your company’s computers to check for weak passwords, what should you do?
A. Change all passwords
B. Tell all employees
C. Disable all accounts
D. Get permission from management
D. Get permission from management
Computer Science & Information Technology
You might also like to view...
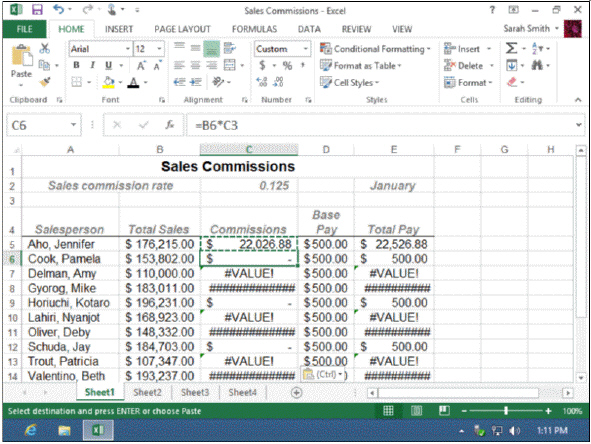 In the accompanying figure, the original formula =B5*C2 works correctly in cell C5. When that formula is copied to cell C7, the relative references in the formula change to _____.
In the accompanying figure, the original formula =B5*C2 works correctly in cell C5. When that formula is copied to cell C7, the relative references in the formula change to _____.
A. =B6*C3 B. =B7*C4 C. =B8*C5 D. =B5*C2
Computer Science & Information Technology
The Office Clipboard can temporarily store only one cut or copied item.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
The ________ function returns one value if a condition is met and a different value if it is not
A) COUNTIF B) IF C) MAX D) MEDIAN
Computer Science & Information Technology
You are limited to declaring a maximum of three variables in a single statement.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology